VIRUSDEFINISJON
Virustype: Virus / skadelig programvare
Også kalt: Backdoor.MSIL.Tyupkin
Hva er catfishing?

Tyupkin er et stykke skadelig programvare som lar nettkriminelle tømme minibanker via direkte manipulasjon. Denne skadelige programvaren, oppdaget av Kaspersky Lab som Backdoor.MSIL.Tyupkin, påvirker minibanker fra en større minibankprodusent som kjører Microsoft Windows 32-biters versjon.
Detaljer om virustrussel
De nettkriminelle jobber i to trinn:
Trinn 1 – Tilgang og infeksjon
Først får de fysisk tilgang til en minibank og setter inn en oppstartbar CD for å installere skadelig programvare – koden kalt Tyupkin ( Backdoor.MSIL.Tyupkin ). Når minibanksystemet har blitt startet på nytt, er den infiserte minibanken under deres kontroll.
Trinn 2 – Kontroll og tyveri
Den infiserte minibanken kjører deretter i en uendelig sløyfe og venter på en kommando. For å gjøre svindelen vanskeligere å identifisere, godtar skadelig programvare Tyupkin bare kommandoer til bestemte tider på søndag og mandag kveld. Det er i disse tidene de nettkriminelle er i stand til å stjele penger fra den infiserte maskinen.
Metodikk
Videoopptak fra overvåkingskameraer ved de infiserte minibankene viste metodene som ble brukt for å få tilgang til kontanter fra automatene. En unik tallkombinasjonstast basert på tilfeldige tall blir nygenerert for hver økt. Dette sikrer at ingen utenfor gjengen ved et uhell kan tjene på svindelen. Deretter mottar den ondsinnede operatøren instruksjoner på telefon fra et annet medlem av den nettkriminelle gjengen som kan algoritmen og er i stand til å generere en øktnøkkel basert på nummeret som vises. Dette sikrer at muldyrene som samler inn kontantene ikke prøver å gjøre det alene.
Når nøkkelen er tastet inn riktig, viser minibanken detaljer om hvor mye penger som er tilgjengelig i hver kontantkassett, og inviterer operatøren til å velge hvilken kassett som skal ranes. Deretter tar minibanken ut 40 sedler om gangen fra den valgte kassetten.
Hvor er det Tyupkin-viruset som infiserer minibanker?
Basert på statistikk hentet fra VirusTotal, har det blitt sett inn skadelige programmer fra følgende land:
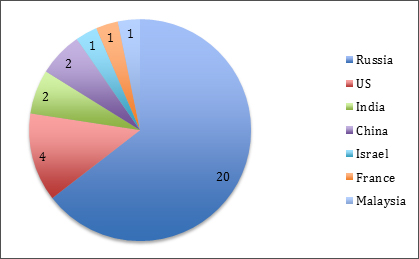
Land der den skadelige programvaren Tyupkin er aktiv
Sikkerhetstips for minibanker for operatører/banker
- Gjennomgå den fysiske sikkerheten til minibankene deres og vurder å investere i sikkerhetsløsninger av høy kvalitet.
- Bytt ut alle låser og primærnøkler på det øvre panseret på minibankene, og ikke vurder å bruke standardinnstillingene gitt av produsenten.
- Installer en alarm og sørg for at den er i god stand. De nettkriminelle bak Tyupkin infiserte bare minibanker uten installert sikkerhetsalarmsystemer.
- Bytt standardpassordene.
- Sørg for at maskinene har oppdatert antivirusbeskyttelse
- Vær på utkikk etter sosialtekniske angrep fra kriminelle som kan utgi seg for å være inspektører, eller sikkerhetsalarmer, overvåkingskameraer eller andre enheter i lokaler.
- Behandle innbruddsalarmer seriøst og handle deretter ved å varsle politimyndighetene om ethvert potensielt brudd.
- Hvis du vil ha råd om hvordan du kan bekrefte at minibankene dine for øyeblikket ikke er infisert, kan du kontakte Kaspersky på intelreports@kaspersky.com . Hvis du vil foreta en fullstendig skanning av minibankens system og slette bakdøren, kan du bruke gratisverktøyet for fjerning av Kaspersky Virus (tilgjengelig for nedlasting her ).
Video: Tyupkin ATM Security Breach
Se videoen om Tyupkin ATM Security Break
Andre artikler relatert til Virustrusler
Relaterte produkter: